Author: Science Team
-
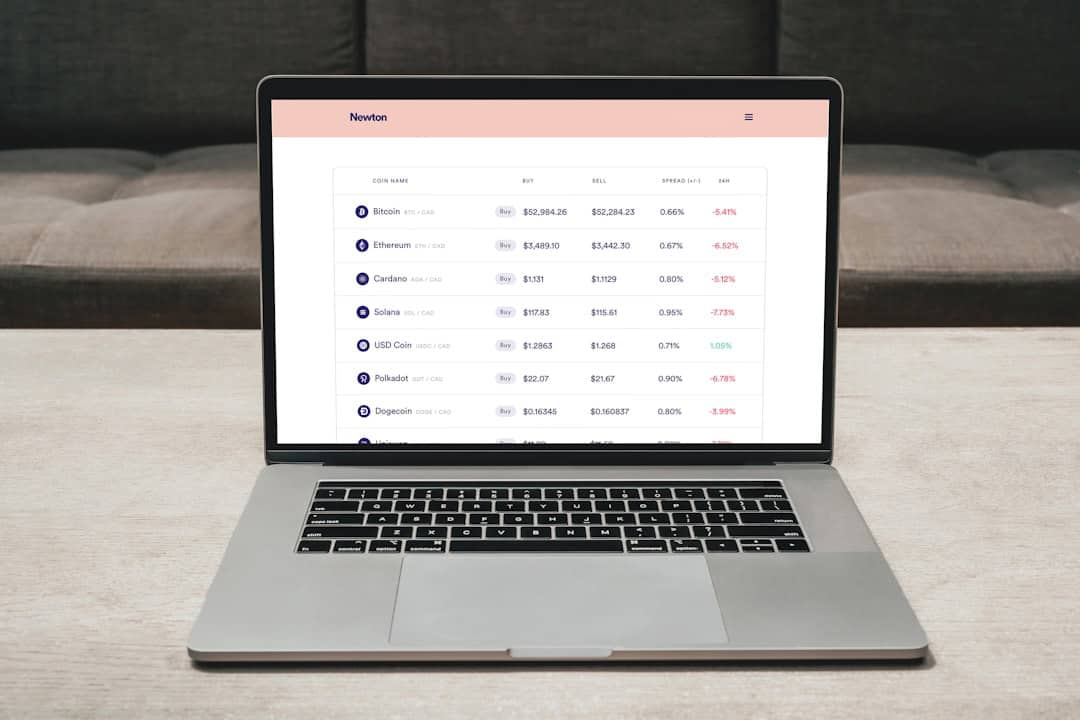
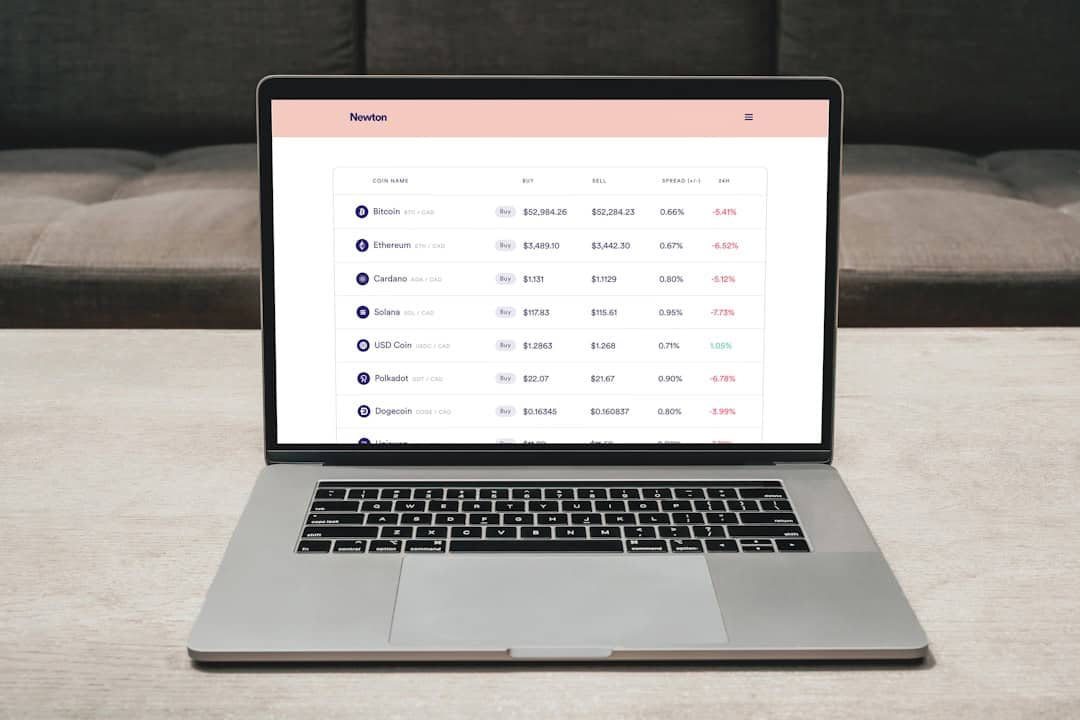
Protecting Your Data: The Importance of TTP in Cyber Security
In the field of cybersecurity, TTP stands for Tactics, Techniques, and Procedures. These elements represent the methods and strategies employed by cyber attackers to infiltrate systems, steal data, or inflict damage. Understanding TTP is essential for Cybersecurity professionals as it enables them to anticipate and defend against potential threats. Tactics refer to the overall strategy…
-

Advancing AI with Multimodal Machine Learning
Multimodal machine learning is a branch of artificial intelligence that develops algorithms and models to process and understand data from multiple sources, including text, images, audio, and video. This approach allows AI systems to learn from and make decisions based on diverse information, similar to how humans perceive and interpret their environment. By combining different…
-

Raising Cyber Security Awareness
In the digital era, cyber security awareness has become increasingly crucial. As technology plays a larger role in communication, financial transactions, and personal data storage, the risk of cyber attacks has escalated. Individuals must understand potential threats and implement proactive measures to safeguard themselves and their personal information. Cyber security awareness enables people to identify…
-
Mastering Geometry: A Guide to Geometric Learning
Geometry is the branch of mathematics that studies shapes, sizes, and spatial properties. It has applications in engineering, architecture, art, and physics. The fundamental elements of geometry include points, lines, angles, and shapes. Points have no size or shape, while lines are infinite collections of points. Angles form when two rays share an endpoint, and…
-

Protecting Networks: Essential Information Security Measures
In the modern digital era, cybersecurity threats are continually evolving, with malicious actors employing increasingly sophisticated attack methods. Organizations face a diverse array of potential security risks, including ransomware, phishing scams, insider threats, and Distributed Denial of Service (DDoS) attacks. It is essential for businesses to remain informed about current threats and vulnerabilities to effectively…
-

Enhancing Predictive Analytics with MATLAB Machine Learning
Predictive analytics is a data-driven approach that utilizes statistical algorithms and machine learning techniques to forecast future outcomes based on historical data. This methodology enables organizations to make data-informed decisions, anticipate market trends, and gain competitive advantages in their respective industries. Machine learning, a subset of artificial intelligence, focuses on developing algorithms that can learn…
-

Defending Networks: The Art of Capture the Flag Cyber Security
Capture the Flag (CTF) competitions are widely recognized as an effective method for honing cybersecurity skills. These events challenge participants to identify and exploit vulnerabilities within simulated environments. The primary objective is typically to obtain a “flag,” which is a digital token or piece of data representing a successful system breach. CTF competitions occur in…
-

Mastering Reinforcement Learning in Python
Reinforcement learning is a machine learning technique that trains agents to make sequential decisions in an environment to achieve specific goals. Unlike supervised learning, which uses labeled data, or unsupervised learning, which uses unlabeled data, reinforcement learning employs a trial-and-error approach. Agents learn from the consequences of their actions, maximizing rewards and minimizing penalties. This…
-

Uncovering Cybersecurity Opportunities with Cyberseek
The cybersecurity job landscape is a dynamic and rapidly evolving field that plays a critical role in protecting organizations from cyber threats. With the increasing frequency and sophistication of cyber attacks, the demand for Cybersecurity professionals has never been higher. Cybersecurity jobs encompass a wide range of roles, including security analysts, penetration testers, incident responders,…
-

Unleashing the Power of Hopfield Networks
Artificial Intelligence (AI) has transformed problem-solving and decision-making across numerous domains. Neural networks, computational models inspired by the human brain’s structure and function, are a fundamental component of AI. Hopfield networks, a specific type of recurrent neural network named after John Hopfield, have garnered considerable interest due to their distinctive properties and AI applications. These…
-

Predictive Power: Machine Learning Graphs
Machine learning graphs have transformed data analysis and prediction. These tools utilize machine learning algorithms to visualize and interpret complex data patterns. They can forecast trends, detect anomalies, and facilitate data-driven decision-making. The predictive capabilities of machine learning graphs have impacted various sectors, including finance, healthcare, and marketing. Machine learning graphs excel at processing large,…
-

Protecting Your Data: The Importance of EDR Cyber Security
EDR (Endpoint Detection and Response) is a vital element of modern cybersecurity strategies. These solutions are specifically designed to monitor and address sophisticated threats targeting endpoints such as computers, laptops, and mobile devices. EDR systems provide organizations with real-time insights into endpoint activities, enabling swift and effective detection and response to potential security incidents. EDR…
-

Predicting Future Trends: Time Series in Machine Learning
Time series analysis is a fundamental component of machine learning that focuses on examining and forecasting data patterns over time. This method involves studying the trends, patterns, and behaviors of data points collected at consistent intervals. Time series data is common across various domains, including finance, economics, meteorology, and numerous others. In the context of…
-
WAF Cyber Security: Protecting Your Online Assets
Web Application Firewall (WAF) is a critical cybersecurity tool designed to protect web applications from various online threats. It functions by monitoring and filtering HTTP/HTTPS traffic between a web application and the Internet, acting as a protective barrier. WAFs inspect all incoming and outgoing traffic to identify and block malicious activities, making them essential for…
-

Mastering Deep Learning with PyTorch
Deep learning is a specialized branch of machine learning that employs artificial neural networks to facilitate machine learning from data. This field has garnered considerable attention in recent years due to its capacity to address complex challenges across various domains, including image and speech recognition, natural language processing, and autonomous vehicle technology. PyTorch, an open-source…
-

Securing Your Cloud Network: Best Practices for Enhanced Security
Cloud network security is a crucial component of an organization’s overall security strategy. As businesses increasingly rely on cloud services and face growing cyber threats, protecting cloud networks has become essential. Cloud network security encompasses safeguarding data, applications, and infrastructure hosted in the cloud from unauthorized access, data breaches, and other security risks. Implementing robust…
-

Unleashing the Power of Convolutional Networks
Convolutional Neural Networks (CNNs) are a specialized type of deep learning algorithm designed for processing structured grid data, particularly images. They have significantly advanced the field of computer vision by automatically learning spatial hierarchies of features from input data. This capability makes CNNs highly effective for tasks including image recognition, object detection, and video analysis.…
-

Securing Cloud Computing Networks: Ensuring Data Protection
Data protection in cloud computing networks is crucial due to the sensitive nature of stored and transmitted information. Cloud computing has transformed business operations by offering scalable and cost-effective solutions for data storage and processing. However, this convenience introduces security risks, as data is stored in remote data centers rather than on-premises servers, making it…
-

Mastering Neural Networks with Python
Neural networks are a crucial element of artificial intelligence (AI), designed to emulate the human brain’s information processing mechanisms. These networks consist of interconnected nodes, or “neurons,” that collaborate to analyze and process complex data. Neural networks have the capacity to learn from data, recognize patterns, and make decisions based on input information. AI, in…
-

Unlocking the Potential of Bing AI
An enhanced artificial intelligence system called Bing AI was created by Microsoft and incorporated into the Bing search engine. In order to understand user queries and provide more accurate search results, it makes use of advanced machine learning algorithms and natural language processing. By gaining knowledge from user interactions, the system is built to continuously…
-

Protecting Networks and Clouds: Ensuring Security
In today’s digital age, network and cloud security are of paramount importance for businesses of all sizes. With the increasing reliance on technology and the internet, the risk of cyber threats and attacks has also grown exponentially. It is crucial for organizations to understand the significance of securing their networks and cloud infrastructure to protect…